
Hi, I am Leonard
leonardmelnik@pm.me
Cybersecurity enthusiast and software developer...
Projects

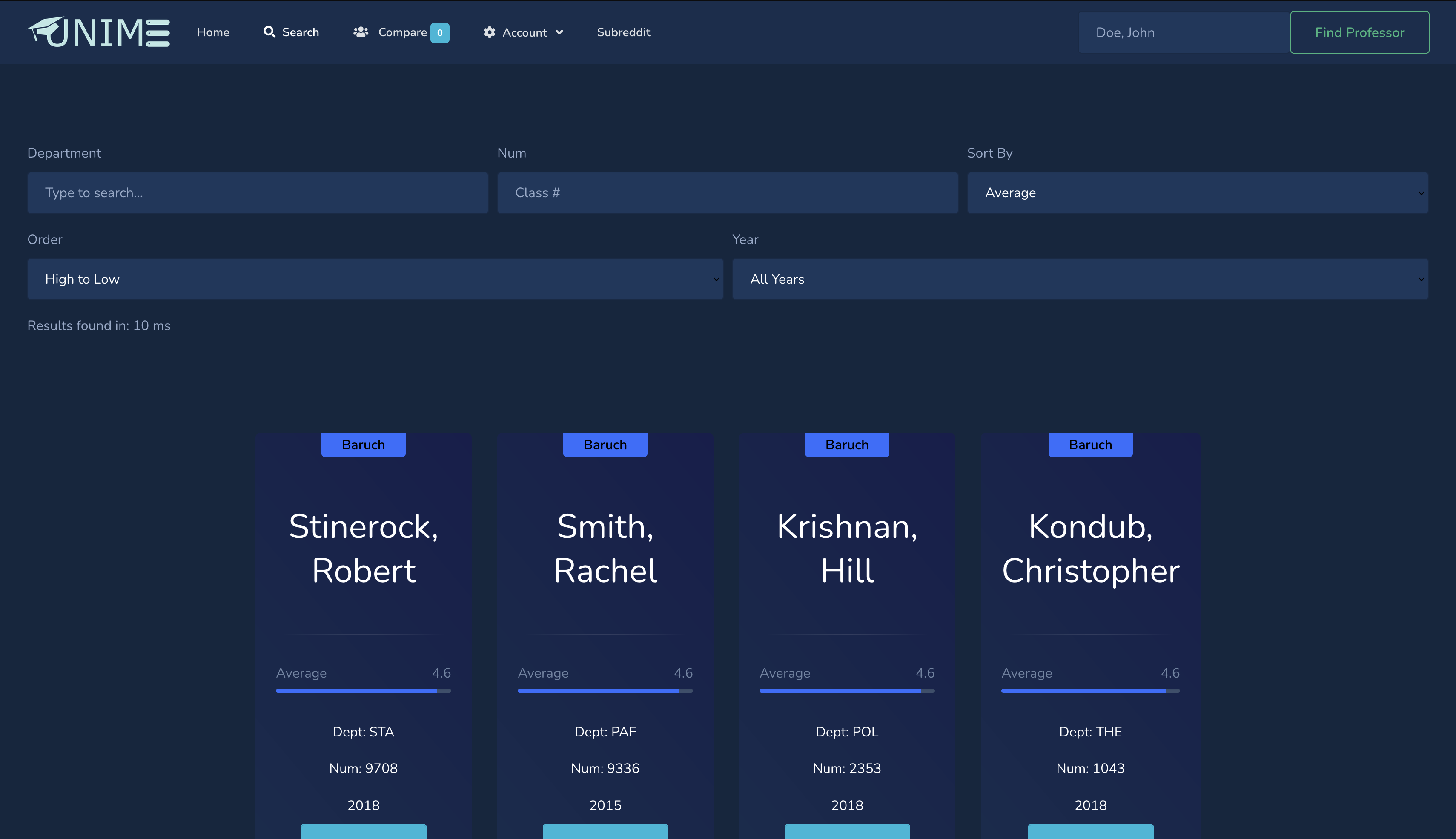
A free tool that displays official Professor evaluation surveys in a comprehensive and concise manner. Initial version had over 10k unique visitors.
BreachByte
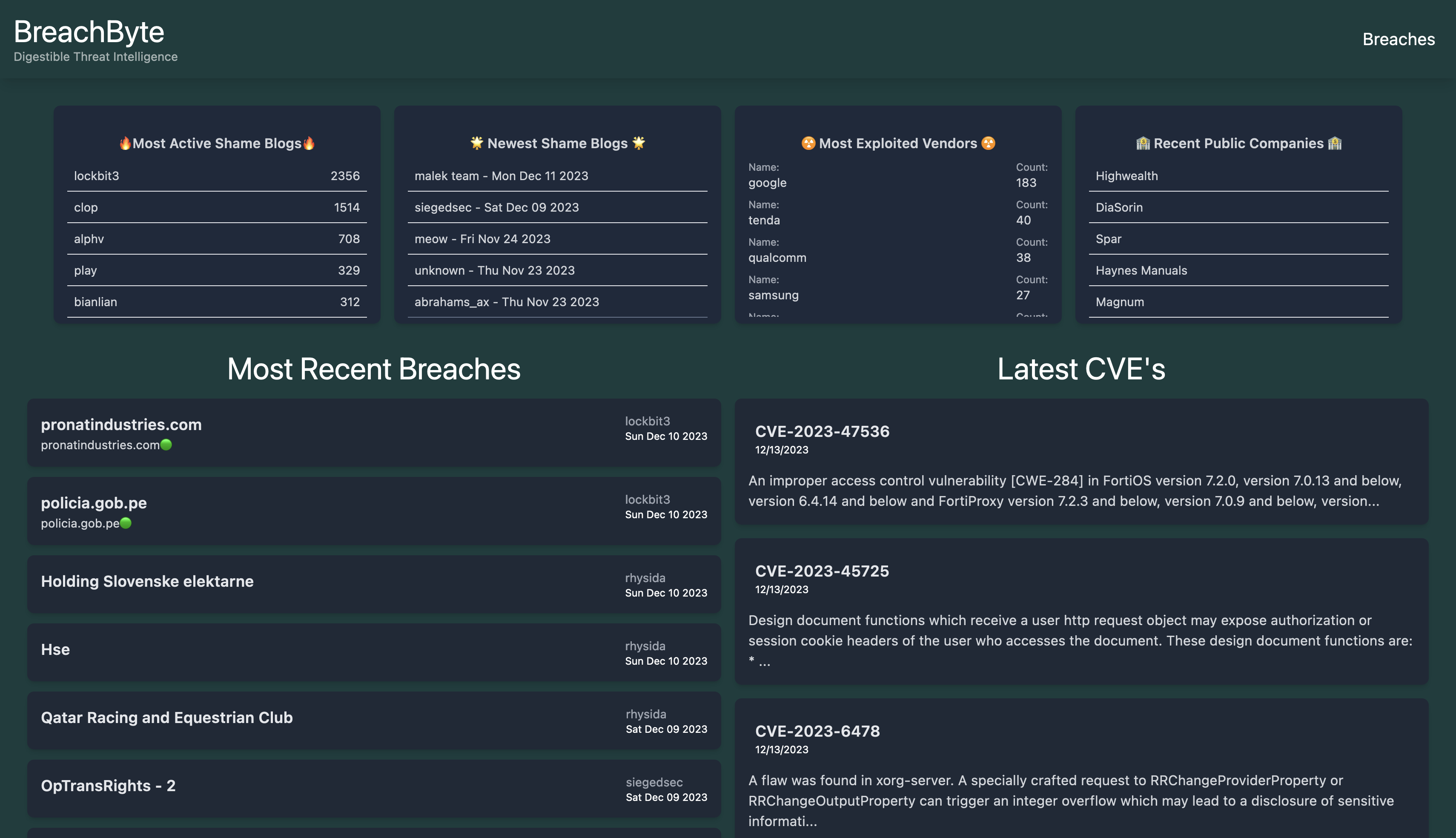
Digestible Threat Intelligence. Free and open tool to view latest breaches.
Evaluable
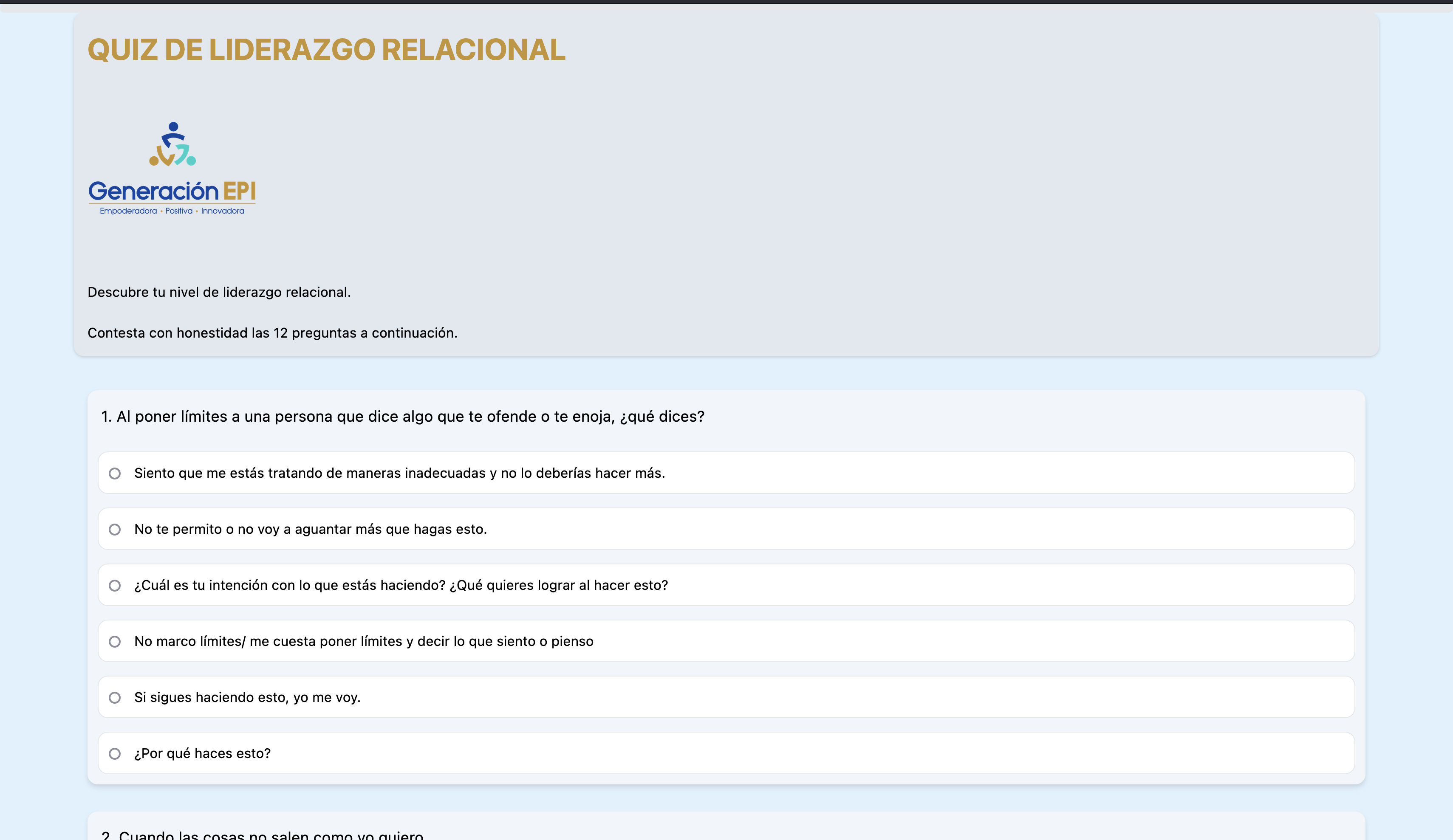
Advanced multi-variate surveying platform currently implemented in several latin-american companies.
SimpleStatus
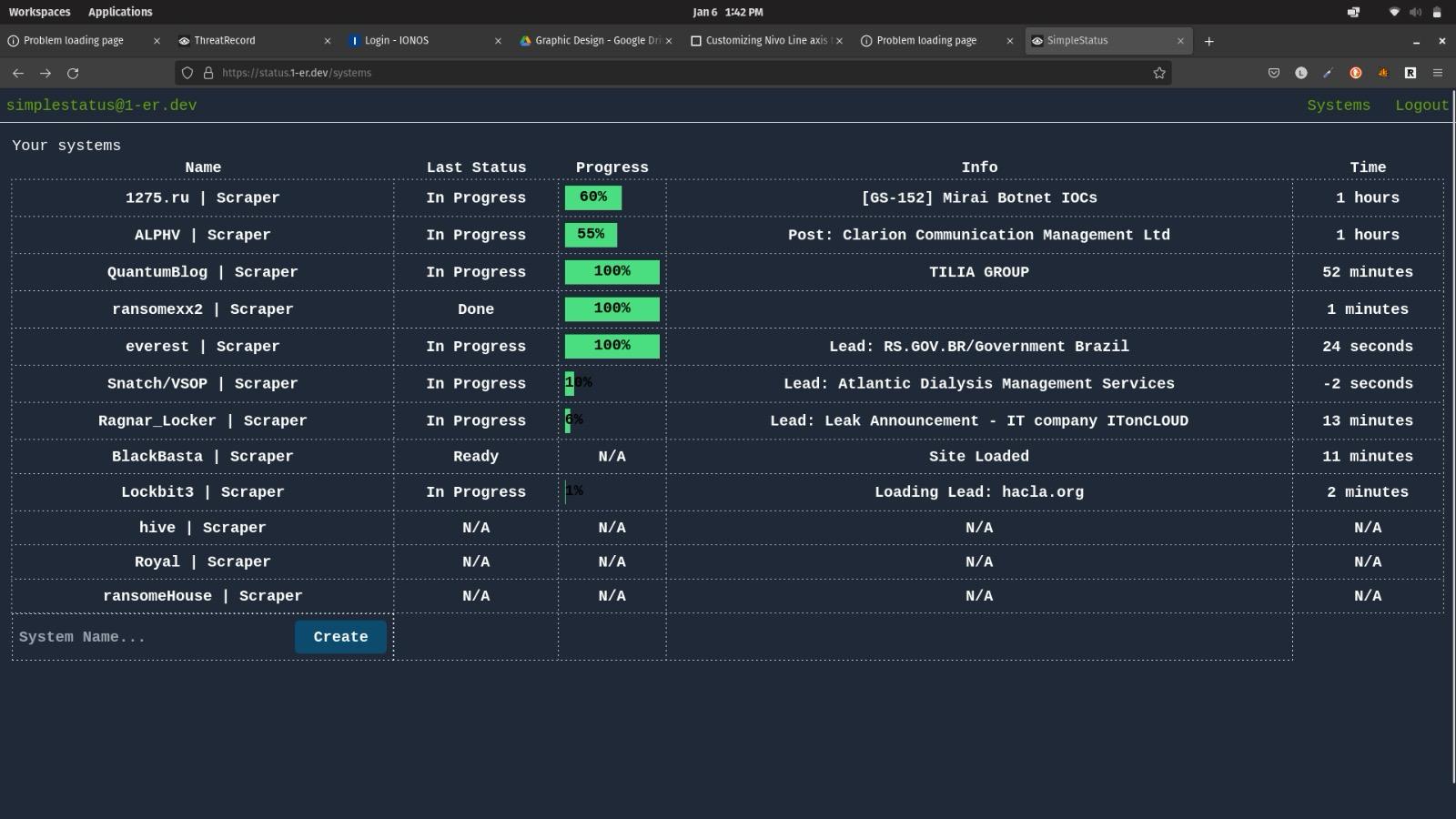
Super basic platform to allow monitoring of processes/scripts/and more
Watchdog
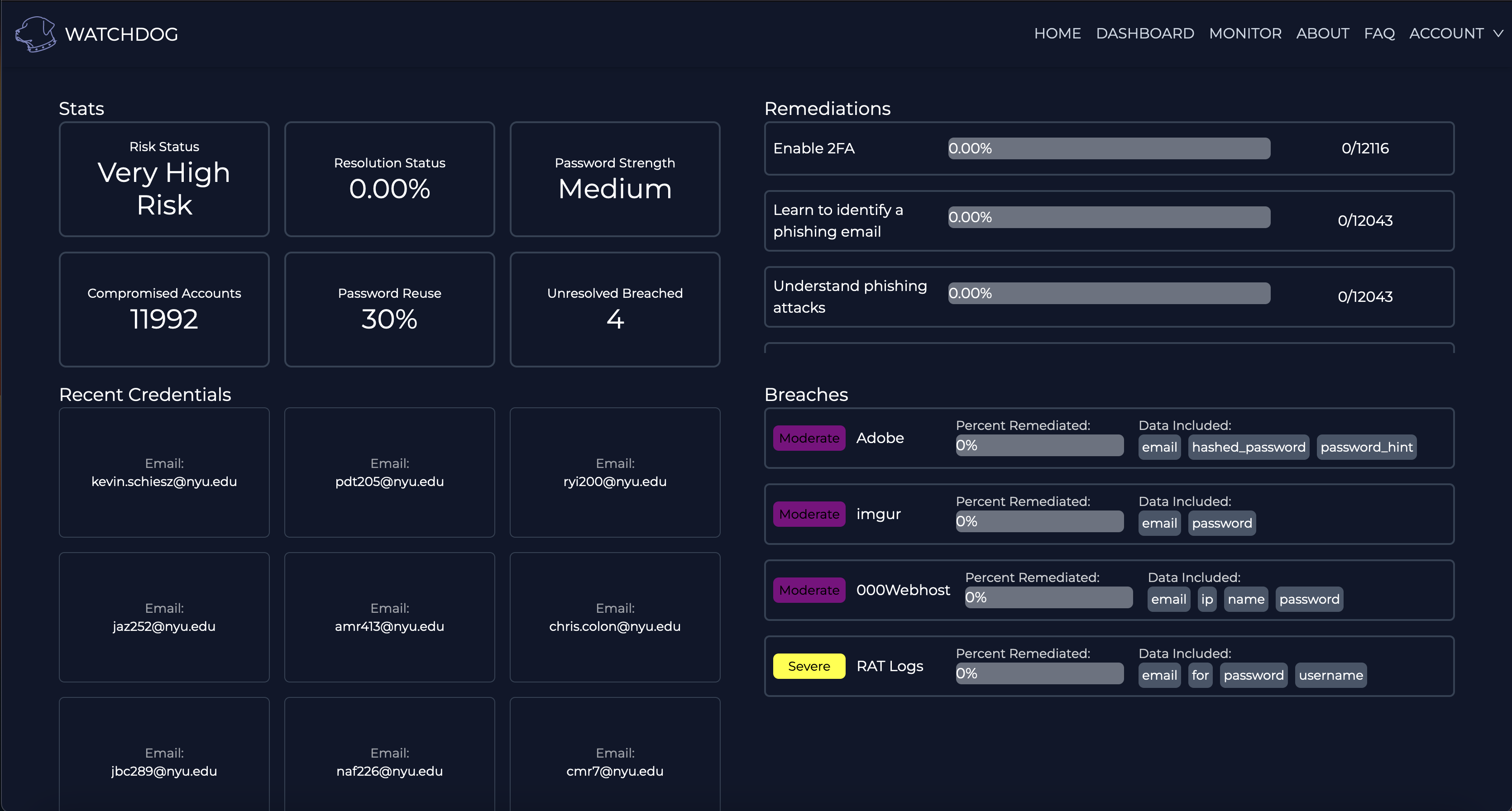
Individual, Family, and Corperate credential monitoring and remediation platform
Watchdog (Web Ext)

Individual, Family, and Corperate credential monitoring and remediation platform

Enigma

Advanced multi-variate surveying platform currently implemented in several latin-american companies.
ThreatRecord
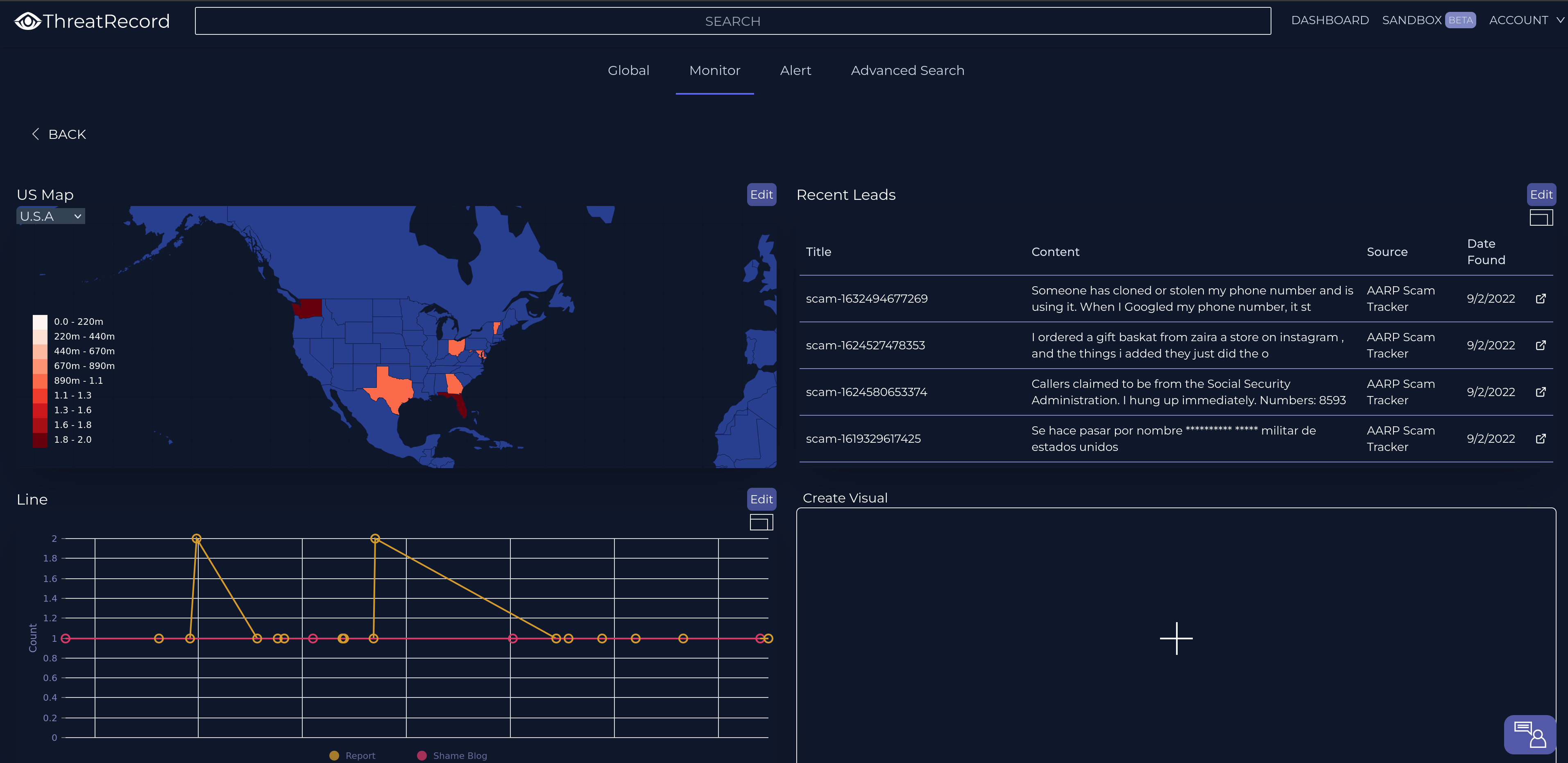
Threat Intelligence platform. Custom Dashboards, Analytics, Alerting with advanced filtering.
Certifications
A showcase of my certifications and qualifications in various domains.

Microsoft Certifications
- Power BI Data Analyst Associate
- Azure AI Fundamentals

Stripe Certified Professional Developer

Kusto Detective Gold Star

Qualys Certifications
- CyberSecurity Asset Management (CSAM)
- Web Application Scanning
- Vulnerability Management Detection & Response
Hubspot Certifications
- Sales Software
- Inbound
- Frictionless Sales
- Revenue Operations

CSI Linux Certified Investigator
Articles/Blogs
Some articles or posts I have written about my work as well as hobbies.
Discussed the criticality of web scanning in preventing data breaches and its impact on reducing escalating costs related to security failures.
Outlines the methods by which credentials are compromised, including database breaches, malware, and phishing, and discusses how digital forensics and law enforcement can acquire these credentials for investigation. The paper highlights the benefits and challenges of using stolen credentials in forensics.
I explore the vulnerability of small businesses to cyber threats and the importance of threat intelligence in mitigating these risks.
This is an older blog post of mine where I used an arduino to run a payload on Windows and Mac machines with persistence.